[ad_1]
It’s World Password Day, and that’s a good opportunity to do something you’ve probably been procrastinating about: Replace your website passwords that hackers stole because of some company’s lax security. Fortunately, your Apple devices make it easy to find out which of your passwords leaked so you can change them.
Fix a potentially serious problem now, before something bad happens..
iCloud Keychain helps you deal with too many passwords
If you’re like me, you probably use unique passwords to log in to hundreds of websites and apps. I have so many I can’t conveniently count them – I stopped at 100 and was still near the top of the list.
Apple makes it easy to store and use your passwords with iCloud Keychain. With it, your Apple device (iPhone, Mac, etc.) remembers passwords for you, and automatically inserts them into websites and apps. All you have to do is verify your identity with Face ID or Touch ID.
This makes it easy for you to use strong passwords and change them periodically, because you never need to remember them. Your computer remembers for you.
But if you don’t ever change passwords, you’re opening yourself up to a criminal using your password to, say, buy a bunch of products on Amazon. Or simply empty your bank accounts.
How to find and change passwords compromised by data breaches
Graphic: Ed Hardy/Cult of Mac
Beyond simply storing them, your Apple device also will warn you if passwords in your iCloud Keychain have been compromised by a data leak. It’s easy to find which ones need to be updated.
This feature is available on iPhone, iPad and Mac. (I’m using iPhone for my example.) And you must be using iCloud Keychain, but that’s something Apple urges you to turn on whenever you set up a new device.
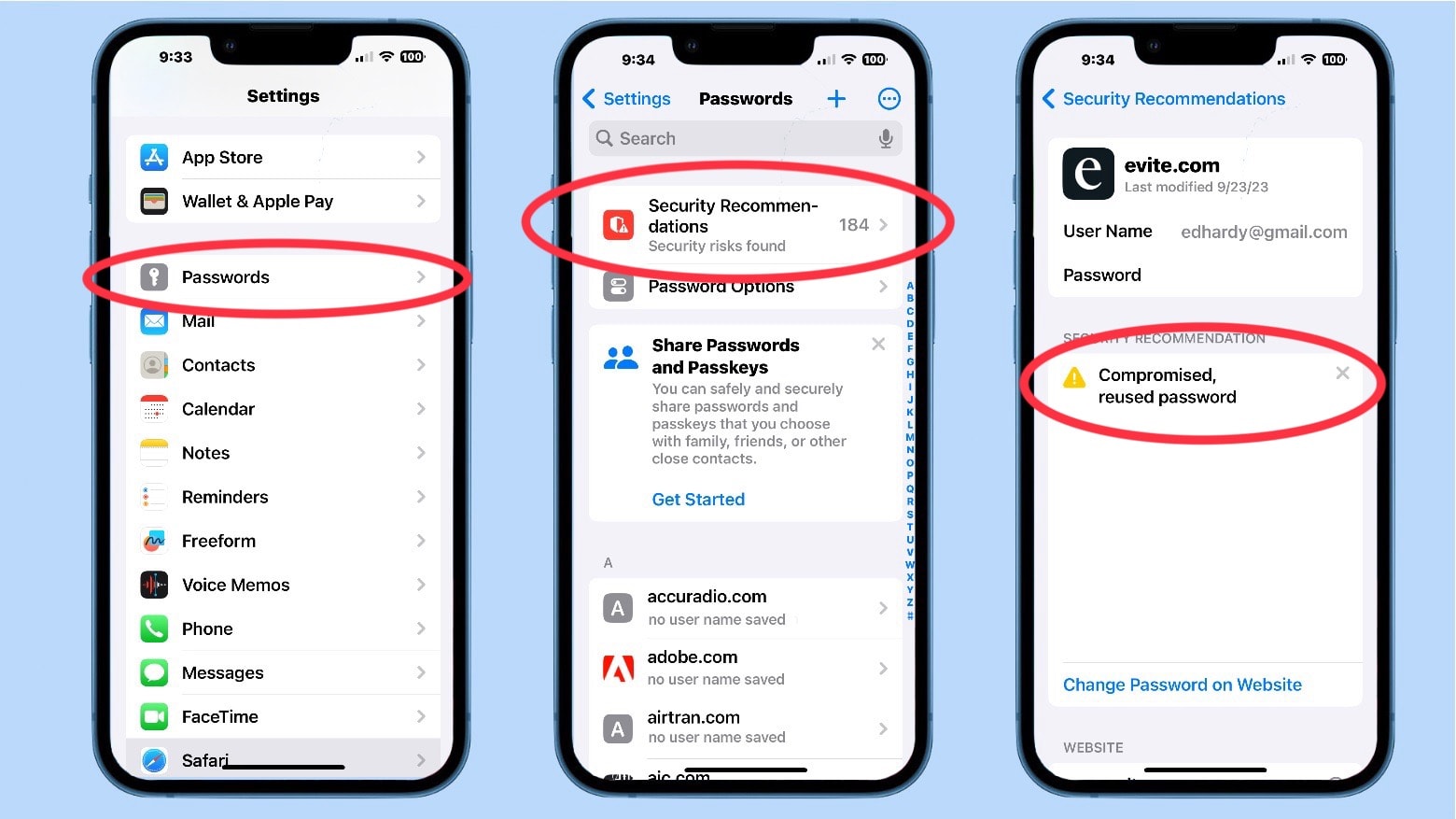
Go to Settings > Passwords. You’ll need to go through Face ID or Touch ID to open this section, of course.
Then look for the Security Recommendations section. Next to this is probably a number. This is how many security problems Keychain has found in your password list. You’ll note I have 184 – I need to take my own advice and update some passwords.
Tap on Security Recommendations to open a list of websites and applications for which your passwords have problems. You are told why for each one, with “this password has appeared in a data leak” being the most common reason.
You have the option to tap on each website for a more detailed description of the security problems. This might include a scolding on reusing passwords.
For each password, you are given the option to Change Password on Website.
An example of changing a Google password via iCloud Keychain
To give you an example of how easy this is, I’ll change the password for one of my Google accounts when going through Passwords in Settings.
While looking at the list of Security Recommendations, I hit Change Password on Website, which opens the Google sign-on screen. I have to sign in to the Google account before I can change the password, obviously. There’s no problem because iCloud Keychain has the user name and current password stored.
Google wants me to go through two-factor authentication so it texts me a code. After I supply this, the screen to enter a new password opens.
The Safari browser is smart enough to figure out that I want to create a new password and automatically suggests a strong one.
Keychain then asks if I should store the new password. I tell it to do so.
And that’s it. The process is very similar with other sites. Or you could just take the iCloud Keychain as a warning and switch over to your favorite web browser, go to the website, and update the password there.
Change passwords the easy way: You’ll be glad you did
I get it – changing passwords is kind of a hassle. I’m the guy with 184 security warnings, after all. But it’s worth it.
Any day you discover someone has used one of your leaked passwords to steal money from you is a bad day. Changing your passwords goes a long way toward preventing that.
[ad_2]
Source Article Link