[ad_1]
El modelo de “pago o consentimiento” ha aparecido en los titulares de toda Europa a medida que los servicios en línea comienzan a traspasar los límites de las normas del RGPD sobre el consentimiento del usuario. Algunas empresas, especialmente las publicaciones de noticias a partir de 2018, comenzaron a solicitar una tarifa para poder optar por no compartir datos y publicidad personalizada. Después de Europa, algunos de los periódicos más leídos del Reino Unido están realizando pruebas Cortafuegos de privacidad.
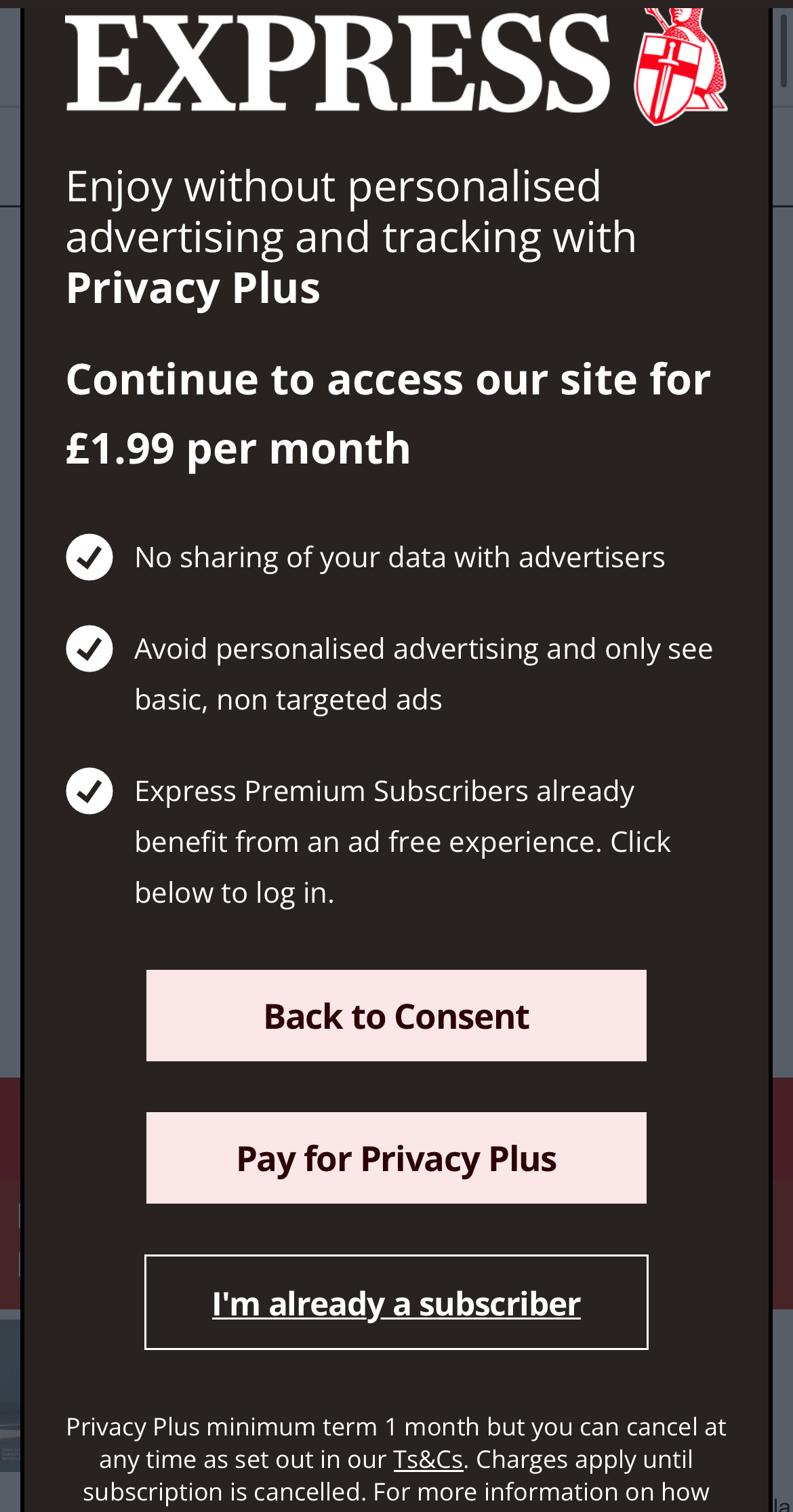
Así es, acceder a noticias gratuitas desde algunos de los sitios de noticias más populares del Reino Unido ahora es costoso: paga una tarifa mensual o renuncia a tus datos personales. La pregunta es: ¿estás dispuesto a pagar el precio de lo que ya debería ser tuyo, tu derecho a la privacidad?
La buena noticia es que puede haber algunas formas de sortear el firewall de privacidad. Sigue leyendo mientras te muestro cómo Mejor VPN Las aplicaciones y otro software de seguridad pueden ayudarle a recuperar su privacidad.
Problema con “Pago o aprobación”
Antes de abordar las soluciones alternativas, echemos un vistazo más de cerca a los problemas de privacidad detrás del modelo de “pago o consentimiento”.
Si bien los sitios de noticias europeos fueron los primeros en probar un firewall de privacidad en 2018, Meta se ha convertido sin duda en el más popular. Tema controvertido En noviembre del año pasado, la organización de derechos digitales Noib, con sede en Austria, fue la primera en presentar una denuncia legal, advirtiendo que este modelo haría de la privacidad un derecho exclusivo.para los ricosDieciocho grupos de consumidores locales hicieron lo mismo con quejas similares.
Según los expertos, este modelo publicitario no es compatible con las leyes de privacidad europeas. Reglamento General de Protección de DatosEl consentimiento de los usuarios debe “darse libremente” para ser válido. La Ley de Servicios Digitales (DSA) también exige que las grandes empresas de tecnología se abstengan de prácticas publicitarias manipuladoras. Mientras que según el artículo 5 de la Ley del Mercado Digital (DMA), estas empresas no pueden beneficiarse del servicio o de algunas funciones sujetas al consentimiento de los usuarios.
Comisión Europea primer vistazo De hecho, descubrió que el nuevo modelo “pagar o aprobar” no era compatible con las reglas de la DMA y le dio a Meta Plazo hasta el 1 de septiembre Para abordar estas preocupaciones, el gigante de las redes sociales ha decidido detener su nuevo plan de pagar publicidad gratuita en el mercado europeo, al menos por ahora.
El entorno de la legislación sobre privacidad del Reino Unido no es tan complejo como el entorno de toda la UE. Sin embargo, después de que el Reino Unido abandonara la UE, el gobierno implementó su propia versión del RGPD que incluía una cláusula de “libre consentimiento”. En marzo de 2023, los reguladores aprobaron otra ley para combatir la llamada fatiga emergente: Ley de Protección de Datos e Información Digital – que amplió el alcance de las exenciones a las cookies y otros requisitos de consentimiento Rastreadores web.
En el momento de escribir este artículo, es difícil determinar si un firewall de privacidad contraviene o no las leyes del Reino Unido. Es probable que las empresas de noticias estén conscientes de esto y hayan decidido probar el asunto antes de que los reguladores emitan una guía más clara al respecto.
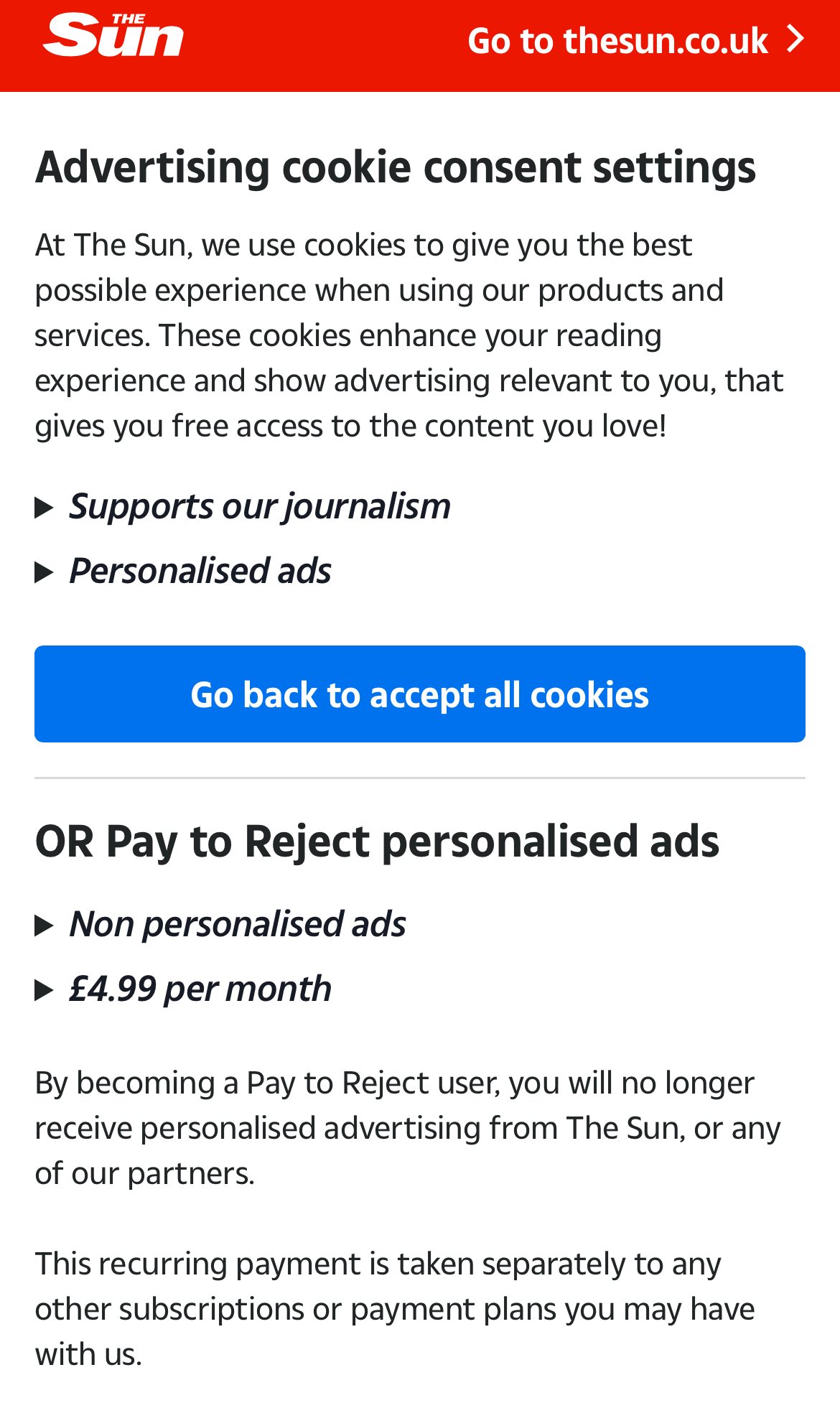
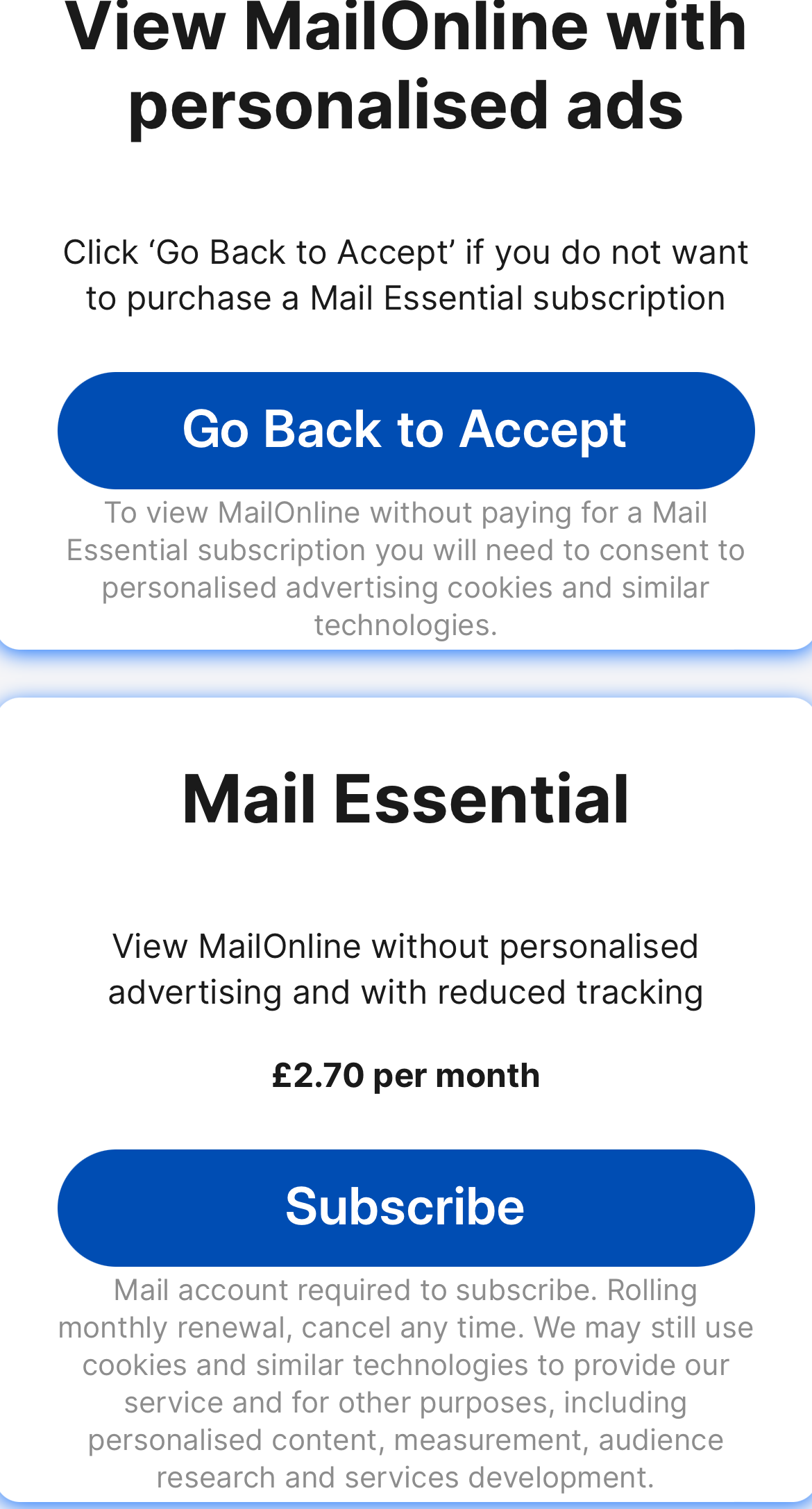
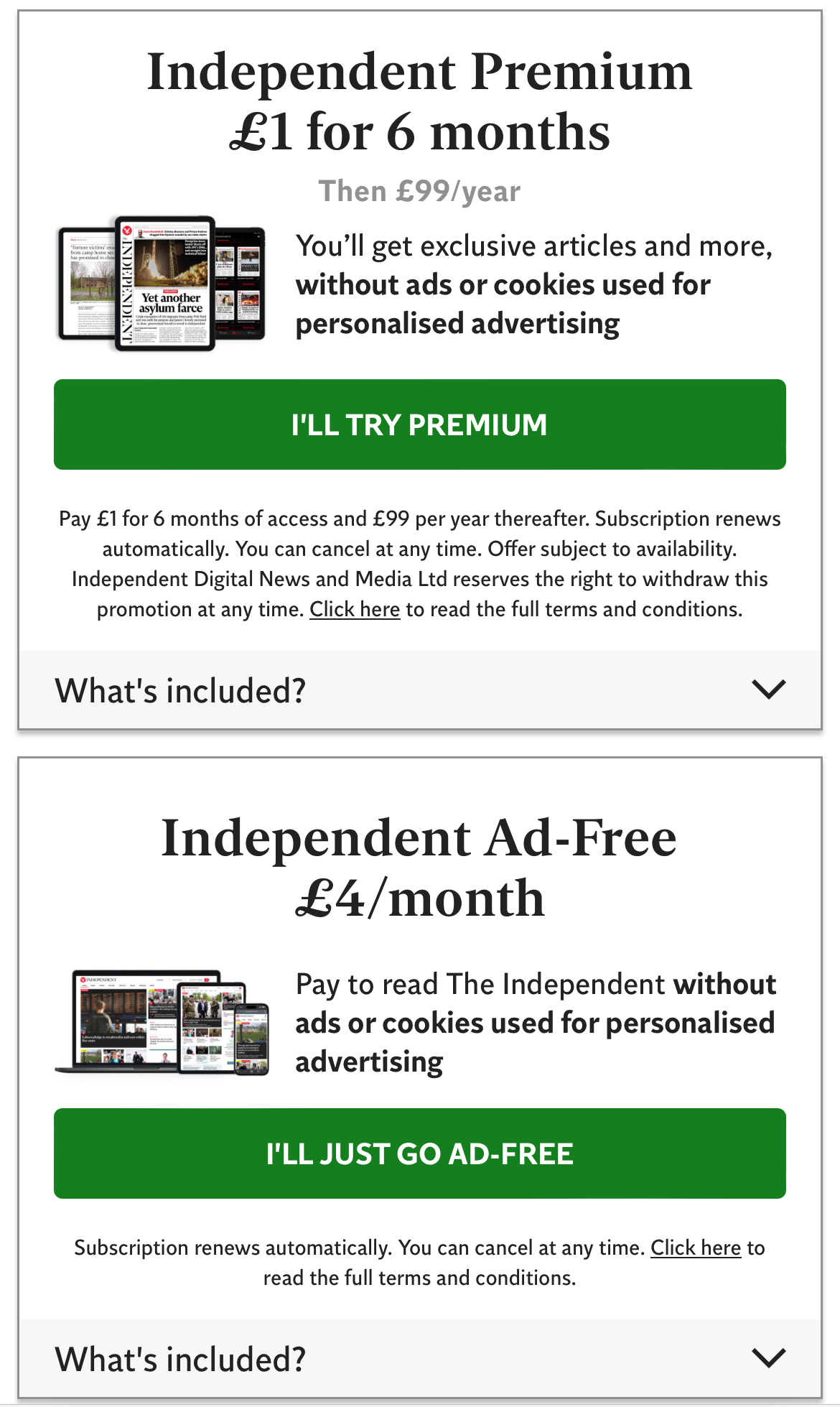
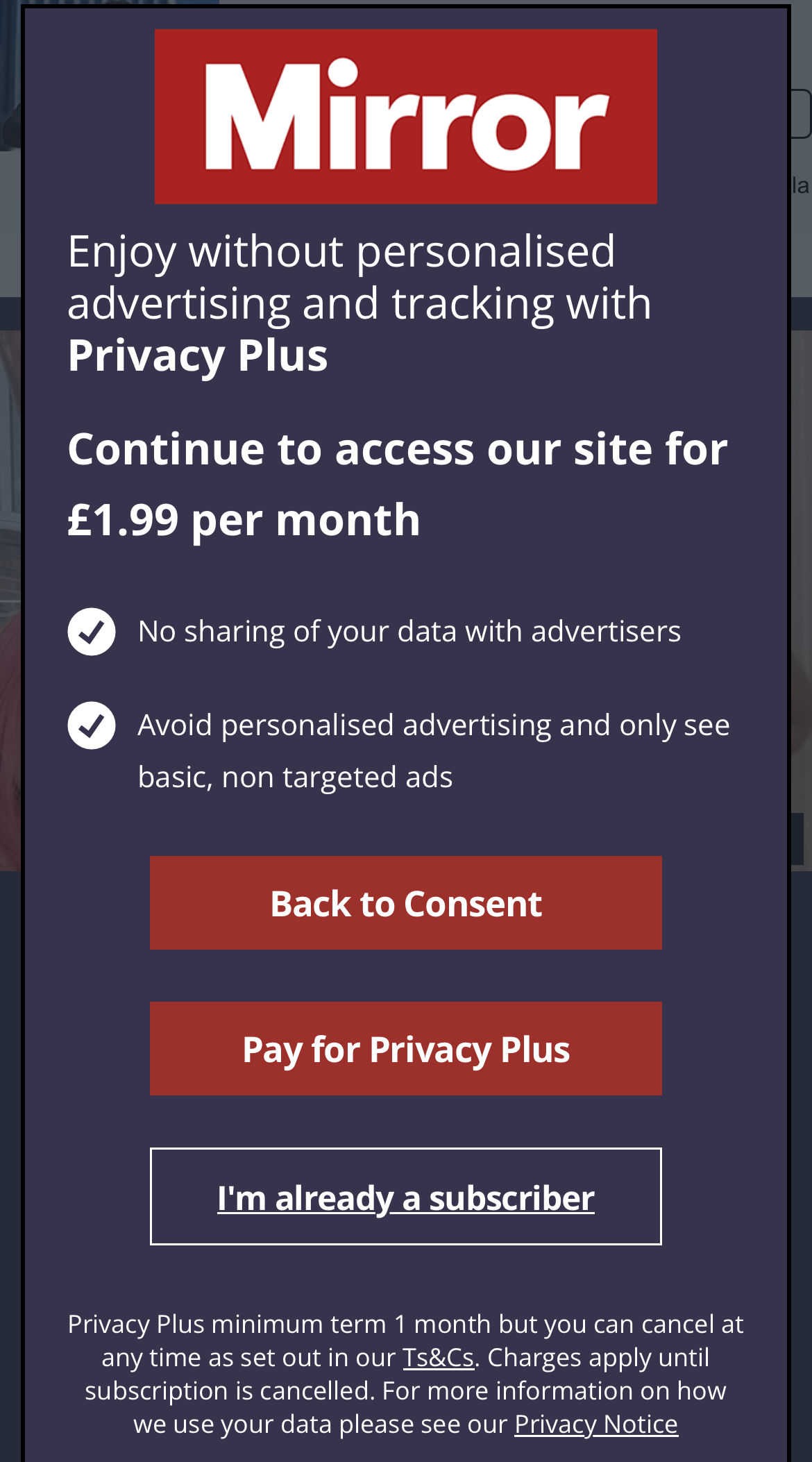
Como muestran las imágenes de arriba, estos periódicos incluyen The Sun y Daily Mail Online, que son algunos de los periódicos más populares del mundo. 24,7 y 23,2 millones de visitantes al mes respectivamente. The Independent, Mirror y Daily Express son otros títulos que intentan sacar provecho de los datos de sus lectores. Sin embargo, el precio de la privacidad varía desde £1,99 por mes hasta un máximo de £4,99 (The Sun). Es probable que se unan más servicios en línea si nadie presiona el botón de detener.
1. Utilice una VPN
La forma más sencilla de evitar el firewall de privacidad es utilizar una aplicación VPN. Para aquellos que no conocen VPN, es la abreviatura de red privada virtual — es un software de seguridad que cifra su conexión a Internet y falsifica la ubicación de su dirección IP real. Ambas habilidades tienen como objetivo mejorar su privacidad en línea, haciendo que sea más difícil ser rastreado en la web.
Al cifrar todos sus datos en tránsito, Las mejores VPN Asegúrate de que nadie pueda ver lo que estás haciendo en línea. Esto se debe a que los sitios web, aplicaciones y otros servicios en línea verán las solicitudes del servidor VPN y no de su dispositivo.
La suplantación de direcciones IP hace que parezca que estás navegando por Internet en un país completamente diferente en poco tiempo. En este caso, puede evitar el cortafuegos de la ley de privacidad conectándose a un servidor ubicado fuera del Reino Unido y también de la UE.
Intenté hacer esto usando las tres mejores VPN según TechRadar: NordVPN, tiburón surfistay ExpressVPN -Y todos funcionan perfectamente.
Cuando se trata de elegir la ubicación VPN adecuada, recomiendo elegir un país con leyes de privacidad estrictas. La conexión con Suiza me resultó muy útil, ya que The Sun, Daily Mail Online y The Independent todavía me dan la opción de rechazar todas las solicitudes no esenciales. Rastreadores webPero esto no funcionó para el Mirror y el Daily Express. Para estas publicaciones, sugiero elegir otros lugares que respeten la privacidad, como Brasil y Nueva Zelanda.
2. Navegando usando Tor
Si no está dispuesto a invertir algo de dinero en un servicio VPN, otra opción para evitar su firewall de privacidad puede ser acceder a sitios de noticias a través de Navegador Tor. Completamente de código abierto y de uso completamente gratuito, Tor cifra su conexión a Internet y oculta su dirección IP real a través de al menos tres capas de seguridad. Cifrado.
Si bien Tor debería funcionar bien como aplicación VPN en papel, obtuve resultados mixtos cuando intenté evadir el firewall de privacidad a través de Tor. En la primera ronda de pruebas (10 de septiembre de 2024), pude acceder a casi todos los sitios de noticias mencionados anteriormente sin exponer todos mis datos. El Daily Express fue el único que fue prohibido.
Estos resultados positivos fueron refutados por otra prueba unos días después (12 de septiembre de 2024). Si bien el Daily Express no fue bloqueado, el firewall de privacidad tampoco fue bloqueado. Lo mismo se aplica a otras publicaciones (The Mirror, The Daily Mail, The Sun). The Independent fue el único sitio que me dio la opción de rechazar todas las cookies.
Así que te recomiendo que lo pruebes tú mismo y veas si funciona para ti. Si no, te sugiero que consigas uno. La mejor VPN gratuita aplicaciones en su lugar. Al momento de escribir este artículo, VPN privada y VPN de protones Son nuestras primeras opciones.
3. Elimina tus datos compartidos
Alternativamente, puede optar por restaurar su privacidad de forma retroactiva. Esto significa que deberá aceptar recibir anuncios personalizados cuando navegue y solicitar la eliminación de sus datos compartidos más adelante.
El “derecho al olvido” es en realidad un derecho garantizado por el Reglamento General de Protección de Datos en la Unión Europea y el Reino Unido. Esta cláusula permite que cualquiera pueda solicitar la eliminación de sus datos personales tanto de las empresas como de los intermediarios de datos.
Es cierto, emitir solicitudes para eliminar su información compartida parece una tarea muy desalentadora. La buena noticia es que Servicios de eliminación de datos Hago este trabajo exactamente para ti.
Servicios como Anónimo Estas herramientas son muy útiles para rastrear y eliminar sus datos de una gran colección de entidades en la web con solo unos pocos clics. Vale la pena tener en cuenta que es necesario pagar una suscripción para utilizar el servicio (a partir de $7.49 por mesSin embargo, esto aún puede resultar más económico que pagar por una experiencia sin publicidad en cada sitio de noticias individualmente.
Probamos y revisamos los servicios VPN en el contexto de usos legales de entretenimiento. Por ejemplo: 1. Acceder al Servicio desde otro país (sujeto a los términos y condiciones de ese Servicio). 2. Proteja su seguridad en línea y mejore su privacidad en línea mientras esté en el extranjero. No apoyamos ni apoyamos el uso ilegal o malicioso de los servicios VPN. No respaldamos ni aprobamos el consumo de contenido pirateado pagado.
[ad_2]
Source Article Link